Update 2009 Sep 28: Do It Yourself PC Phone Home
Update: I left three separate tech service requests with Brigadoon Software, the makers of PCPhoneHome, two by email and one by telephone. The most-recent of those, the phone call, was five days ago and the oldest was more than a week ago. I have received no response yet.
It's my current opinion that PCPhoneHome is an orphan - nobody home at Brigadoon Software. So what if my PC was stolen and it did phone home? I seriously doubt I would get any help tracing it. Apparently it's still possible to order the product, but I won't!
Now the problem is that it's still phoning home, from my home, every day at least twice. Brigadoon's documentation implies that it is nearly impossible to uninstall it without their help, and they don't call back. Since PCPhoneHome puts other "hooks" into the operating system, I think I will try to uninstall it anyway before the trial period expires.
Saturday, February 2, 2008
Monday, January 28, 2008
PCPhoneHome Not Recommended
Update 2009 Sep 28: Do It Yourself PC Phone Home
What if I left my laptop in the car for a moment, and someone ripped it off? or, perish the thought, someone broke in and took my nice new computer? It happens all the time, especially in the corporate and public sectors, but certainly it happens to private individuals too. One in 14 laptops is stolen, say some experts.
But what if that stolen laptop or computer was powered up by the thief, then connected to the internet, and it sent an email back to the original owner describing where it was? And what if "someone" could then tell the police the name and address of the thief?
That's what PCPhoneHome is supposed to do. It costs $30, a modest one-time charge. There is a Windows version and a Mac version. You install it on the hard drive of the computer, and whenever the computer gets a new internet connection it sends an email to any email address that you specify. This happens regularly, day after day, and unless the computer is stolen it's of little use except to let you know that it is still working. But if the computer is stolen, that email contains vital information including the IP address of the computer on its local network, if any, and especially the IP address of the mail server from which the email is actually sent. That IP address can be traced back to the user who was connected to the mail server at that time.

Brigadoon software, the makers of PCPhoneHome, promise to help with the task of tracing the computer and contacting the police with that information. So, for the price of $30, you are buying an insurance policy that may get your computer back, assuming that Brigadoon will actually answer their telephone and trace the PC, and that the police will take the time to retrieve the PC.
I downloaded three trial copies:
Laptop running Windows XP:
Version 3.0 is the "standard" version set up for a 30-day trial. It doesn't say that it works on Vista, but it does on XP. It installed with no problems, I filled out the form with details of my laptop computer (make, model, serial#, more...) and it immediately sent its first email to the address that I specified in the form. The laptop was connected by WiFi, and when I connected it directly to the LAN it sent another email. In fact, it sends TWO emails every time, with a slightly different FROM address, for some reason. No problem. So far, after three days, it works just fine.
New home-built desktop running Vista Ultimate 64-Bit:
I knew that Version 3.0 was not recommended for Vista, even though that was the standard trial download from Brigadoon Software. So I downloaded a 3.2 "upgrade" version and tried installing that, with a subsequent comedy of errors:
Wow I'm SO SORRY that I tried PCPhoneHome on this computer. I tried downloading the official trial version and installing that first, as most users would do. Of course it didn't work, because that version is not for Vista, so then I downloaded the upgrade and tried to install that on top of the first install. The resulting comedy of errors totally eclipsed anything that I had encountered with the desktop installation, and it still doesn't work. I have installed a lot of software on many different machines, but this takes the cake. I have requested a technical service response by telephone and by email, but so far have not received any.
Bottom line: I DO NOT RECOMMEND PCPhoneHome FOR VISTA.
In my opinion, it works fine on XP but is not ready for Vista yet. It phones home on only one of my two Vista installations. There is a workaround for the XYZ "unknown program" prompt at bootup, but that workaround simply trades one security risk for another. Brigadoon Software must fix that problem somehow, perhaps by getting valid "digital signatures" for their software.
Perhaps this is all my fault for installing it on both Vista systems incorrectly. But I don't think so; I suspect anyone running Vista with UAC turned on will experience similar problems. If true, that's an astounding failure, since:
Other Issues:
What if I left my laptop in the car for a moment, and someone ripped it off? or, perish the thought, someone broke in and took my nice new computer? It happens all the time, especially in the corporate and public sectors, but certainly it happens to private individuals too. One in 14 laptops is stolen, say some experts.
But what if that stolen laptop or computer was powered up by the thief, then connected to the internet, and it sent an email back to the original owner describing where it was? And what if "someone" could then tell the police the name and address of the thief?
That's what PCPhoneHome is supposed to do. It costs $30, a modest one-time charge. There is a Windows version and a Mac version. You install it on the hard drive of the computer, and whenever the computer gets a new internet connection it sends an email to any email address that you specify. This happens regularly, day after day, and unless the computer is stolen it's of little use except to let you know that it is still working. But if the computer is stolen, that email contains vital information including the IP address of the computer on its local network, if any, and especially the IP address of the mail server from which the email is actually sent. That IP address can be traced back to the user who was connected to the mail server at that time.

Brigadoon software, the makers of PCPhoneHome, promise to help with the task of tracing the computer and contacting the police with that information. So, for the price of $30, you are buying an insurance policy that may get your computer back, assuming that Brigadoon will actually answer their telephone and trace the PC, and that the police will take the time to retrieve the PC.
I downloaded three trial copies:
Laptop running Windows XP:
Version 3.0 is the "standard" version set up for a 30-day trial. It doesn't say that it works on Vista, but it does on XP. It installed with no problems, I filled out the form with details of my laptop computer (make, model, serial#, more...) and it immediately sent its first email to the address that I specified in the form. The laptop was connected by WiFi, and when I connected it directly to the LAN it sent another email. In fact, it sends TWO emails every time, with a slightly different FROM address, for some reason. No problem. So far, after three days, it works just fine.
New home-built desktop running Vista Ultimate 64-Bit:
I knew that Version 3.0 was not recommended for Vista, even though that was the standard trial download from Brigadoon Software. So I downloaded a 3.2 "upgrade" version and tried installing that, with a subsequent comedy of errors:
- First, the installation program failed to run because, according to Windows, I did not have sufficient privileges to run it even though I was logged on as administrator;
- So I clicked on the installation program's Properties, then Compatibility, and selected "Run as Administrator;"
- Then the installation program went a lot farther, but eventually reported a different error;
- It continued past that error and put up the "registration" screen which takes data to be included in the email that PCPhoneHome sends, but because of the reported error I didn't bother to fill out the screen;
- Nevertheless, the installer said the installation was successful, though I knew better;
- I uninstalled it (still possible until reboot), and tried again;
- Same results, so I rebooted;
- PCPhoneHome disappeared from the list in Programs and Features - it could no longer be uninstalled. This is a security feature built into PCPhoneHome;
- So I "reverted" the drive to the most recent restore point, deleted one leftover executable, and started over;
- This time, surprisingly, the installation went well. I filled out the "registration" screen and allowed it to reboot the computer.
- After logon, Windows alerted me that an "unknown" program XYZ (I won't disclose the name here) wanted to run and asked me if that was OK;
- I said yes. Pretty soon I received the two emails. Yay!;
- Sadly, though, upon each succesive reboot, Windows continues to ask whether program XYZ can run;
- I have modified "User Account Control" (UAC) in Windows Vista so that this no longer occurs, but of course this modification is unacceptable for the long term. UAC is a pain in the ass, but it has a purpose and should be turned ON for day-to-day activities.
- I requested a technical service response by email on January 25, but so far have not received any.
Wow I'm SO SORRY that I tried PCPhoneHome on this computer. I tried downloading the official trial version and installing that first, as most users would do. Of course it didn't work, because that version is not for Vista, so then I downloaded the upgrade and tried to install that on top of the first install. The resulting comedy of errors totally eclipsed anything that I had encountered with the desktop installation, and it still doesn't work. I have installed a lot of software on many different machines, but this takes the cake. I have requested a technical service response by telephone and by email, but so far have not received any.
Bottom line: I DO NOT RECOMMEND PCPhoneHome FOR VISTA.
In my opinion, it works fine on XP but is not ready for Vista yet. It phones home on only one of my two Vista installations. There is a workaround for the XYZ "unknown program" prompt at bootup, but that workaround simply trades one security risk for another. Brigadoon Software must fix that problem somehow, perhaps by getting valid "digital signatures" for their software.
Perhaps this is all my fault for installing it on both Vista systems incorrectly. But I don't think so; I suspect anyone running Vista with UAC turned on will experience similar problems. If true, that's an astounding failure, since:
- The most-easily-stolen computers are laptops;
- Almost all laptops sold in the last YEAR run Vista;
- UAC is turned on by default in all new Vista systems;
- Brigadoon Software had months BEFORE THAT to prepare for Vista; so
- They are about two years behind the curve and falling further behind daily.
Other Issues:
- If your computer is stolen and does phone home, will Brigadoon Software actually answer their telephone and trace an email for you? When I called their telephone number this afternoon during regular business hours, I got an answering machine and no callback today. This is not what you want, because the computer may soon evaporate into the black market and never call home again. I see other remarks on the internet which indicate that this is a real question. I will update this post and add a new post when/if I hear from them regarding my pre-sales technical service problems.
- One very good thing: My computers are set up to require a password for my own logon, to prevent access to my account through the network, and also through the keyboard if the computer were to be stolen. On both the XP and the Vista desktop system, if I booted up and did NOT log on, the computer sent the email anyway. Thus if a thief were sitting at the keyboard trying various passwords, and made the mistake of connecting the computer to the internet first, the email would be on its way.
- But what if the thief didn't connect to the internet before logging on? In another part of the FAQ document, Brigadoon goes into great detail to show how to set up a computer so that it will boot up with one account which does NOT have a password. They don't spell out WHY we should do that, because it obviously reduces the system's security. But I suppose if I were the thief, I might try each of the usernames on the logon screen, looking for one with no password. If found, I might start with that account, and might even use that account to connect to the internet. Obviously, that account should not have administrator privileges!
- Brigadoon makes another good point in their FAQ document: It's important to set up a password to the BIOS of a computer, and then set the BIOS to boot first from hard disk, not floppy or CD/DVD or memory stick. This prevents a thief from using an alternate boot to simply reformat the disk and install a new operating system, thereby obliterating the PCPhoneHome program. In case YOU have a problem with the hard disk, you simply enter the password and change the BIOS back to allow boot from alternate devices. Of course the thief can still remove the hard drive and reformat it some other way, but that's more work and by then the computer may already have phoned home.
Tuesday, January 8, 2008
Google Desktop vs. Copernic
The basic idea: What if I could search my own computer as easily as I can search the web? Then I could find an email or a Word document, even a PDF document, or a previously-viewed web page, or all of those on my own computer in an instant, just by entering a few words of text that I think might be in the document or in its name.
Enter Google Desktop (GD). I discovered this a year or two ago, when I was running Windows XP, and thought it was slicker than sliced bread. Well, almost, and certainly better than anything that Microsoft offered. It didn't work exactly right - sometimes I would click on a result and nothing would come up - but at least it did seem to find everything.
Except WordPerfect documents. I use WordPerfect and certainly prefer it to Microsoft Word, but the documents apparently have a unique format and are not correctly indexed by GD or by Microsoft's Vista indexing software. No surprise that Microsoft would deliberately omit WordPerfect, because they have been trying to bury it with Word for years (with obvious success), but we expect better from Google. There is a contributed Google Desktop plugin called Larry's WordPerfect Indexer, and it seemed to work when installed, but Google Desktop kept uninstalling it for some reason; I never solved that problem.
Enter Windows Vista; I have the 64-bit version. It supposedly has its own indexing, but I find that awkward and obtuse; I still haven't entirely figured what IS and what IS NOT indexed. Google Desktop was better.
However, if you Google "google desktop" and "vista" you will find complaints about Google Desktop slowing down Vista, and you will find that Google and Microsoft are having a legal hassle. Nevertheless a few days ago I downloaded GD and installed it. To my surprise, GD did not offer ANY indexing commands. I could not make it re-index, and there was no pause-indexing command. When I did a GD search it DID come up with results though, without ever doing an indexing search. From this I assume that it uses Vista's built-in index, and no longer builds its own index. I "installed" Larry's WordPerfect Indexer, but of course a search still did not bring up any WordPerfect documents. Conclusion: At least for now, Google Desktop is broken - no better than Vista's search, which itself is very clumsy and which will apparently never be able to search WordPerfect documents.
 Enter Copernic. I downloaded this desktop searcher and couldn't be more pleased. It runs exactly the same on both XP (my laptop) and Vista 64 (my new desktop computer). In both cases it built its index in almost no time at all. Here are some of the features:
Enter Copernic. I downloaded this desktop searcher and couldn't be more pleased. It runs exactly the same on both XP (my laptop) and Vista 64 (my new desktop computer). In both cases it built its index in almost no time at all. Here are some of the features:
I've only had Copernic for a couple of days now, but it sure seems far more robust than the competition, and yet easier to use. Unlike those, it's a completed, working product. If I continue to like it, I may just turn off Vista indexing altogether.
Please let me know if you agree, or disagree, or want more information.
Enter Google Desktop (GD). I discovered this a year or two ago, when I was running Windows XP, and thought it was slicker than sliced bread. Well, almost, and certainly better than anything that Microsoft offered. It didn't work exactly right - sometimes I would click on a result and nothing would come up - but at least it did seem to find everything.
Except WordPerfect documents. I use WordPerfect and certainly prefer it to Microsoft Word, but the documents apparently have a unique format and are not correctly indexed by GD or by Microsoft's Vista indexing software. No surprise that Microsoft would deliberately omit WordPerfect, because they have been trying to bury it with Word for years (with obvious success), but we expect better from Google. There is a contributed Google Desktop plugin called Larry's WordPerfect Indexer, and it seemed to work when installed, but Google Desktop kept uninstalling it for some reason; I never solved that problem.
Enter Windows Vista; I have the 64-bit version. It supposedly has its own indexing, but I find that awkward and obtuse; I still haven't entirely figured what IS and what IS NOT indexed. Google Desktop was better.
However, if you Google "google desktop" and "vista" you will find complaints about Google Desktop slowing down Vista, and you will find that Google and Microsoft are having a legal hassle. Nevertheless a few days ago I downloaded GD and installed it. To my surprise, GD did not offer ANY indexing commands. I could not make it re-index, and there was no pause-indexing command. When I did a GD search it DID come up with results though, without ever doing an indexing search. From this I assume that it uses Vista's built-in index, and no longer builds its own index. I "installed" Larry's WordPerfect Indexer, but of course a search still did not bring up any WordPerfect documents. Conclusion: At least for now, Google Desktop is broken - no better than Vista's search, which itself is very clumsy and which will apparently never be able to search WordPerfect documents.
 Enter Copernic. I downloaded this desktop searcher and couldn't be more pleased. It runs exactly the same on both XP (my laptop) and Vista 64 (my new desktop computer). In both cases it built its index in almost no time at all. Here are some of the features:
Enter Copernic. I downloaded this desktop searcher and couldn't be more pleased. It runs exactly the same on both XP (my laptop) and Vista 64 (my new desktop computer). In both cases it built its index in almost no time at all. Here are some of the features:- It automatically indexes WordPerfect documents - important to me if not to you;
- You can select the types of files it will index, including PDF documents and ZIP folders, by type extension;
- You choose whether the indexing function pauses while you use the computer, and if so, for how long;
- You choose which folders you index and which you do not. For example, I have files that are encrypted and certainly don't want them in the index!;
- Regardless how the index is built, you can limit a search to any particular file type, to avoid getting too many results;
- For any specific class of files you can limit the search by date, partial file name, folder, and other attributes;
- There is a quick and easy way to check for updates to Copernic;
- I haven't even discovered all of the features yet.
I've only had Copernic for a couple of days now, but it sure seems far more robust than the competition, and yet easier to use. Unlike those, it's a completed, working product. If I continue to like it, I may just turn off Vista indexing altogether.
Please let me know if you agree, or disagree, or want more information.
Labels:
64-bit,
Copernic,
data encryption,
Google Desktop,
Vista
Friday, December 14, 2007
AverMedia AVerTV Combo PCI-E Media Center Upgrade Kit
Recording TV Programs:
Our ancient VCR (tape recorder) in the TV room is starting to act up and we are looking around for a replacement. Of course VCR is the technology of the previous century - we should probably get a DVD recorder or, better yet by far, a DVR (digital video recorder).
Enter the brand new computer. It turns out that a computer with a TV tuner card can make a dandy DVR, and this new one with lots of power, high-quality graphics, and Windows Vista Ultimate with Media Center is a perfect candidate.
TV Tuner Card:
I have Windows Vista 64 with Media Center, so I ordered the AverMedia Media Center Upgrade Kit from NewEgg.com, a PCI-E tuner card. I chose that product for its features but even more because of the good recommendations from purchasers on NewEgg.com. The card includes two tuners, one for analog channels (broadcast or cable) and the other for digital (broadcast or cable).
Installation:
I installed it in a PCI-E slot, rebooted, and Windows automatically installed the drivers. There was no need to use the drivers on the included CD-ROM; I'm confident that Windows used appropriate drivers. With the kit also came a remote control and remote receiver, for which Windows also found and installed a driver.

I connected the cable TV signal to the analog tuner, and the included "test" antenna to the digital tuner, and immediately tuned in all of the analog cable channels and eight digital broadcast channels.
I'm not an HDTV enthusiast, at least not yet. I know almost nothing about home-theater PC (HTPC). But this was trivially simple. What we have here is a card that is designed to work specifically with Windows Media Center (MC), a Microsoft software package found on some XP and Vista machines. The card came with no other software except drivers - it would be useless without MC, and MC cannot play or record TV signals without a TV tuner card. They go together hand in glove, and they worked together right out of the box with no coaxing at all.
Performance:
It works exactly as advertised and I'm glad to have it. I wonder if we should just build another, cheaper computer and dedicate it to DVR as a replacement for the VCR. Still expensive I guess.
An alternative is to rent the DVR from our cable provider Comcast, which would require us to upgrade the cable from Standard to Digital, and the rental plus the upgrade would cost us $16.00/month or about $200.00/year. At that rate we coud pay for an $800 computer in four years ... hmmm.
Our ancient VCR (tape recorder) in the TV room is starting to act up and we are looking around for a replacement. Of course VCR is the technology of the previous century - we should probably get a DVD recorder or, better yet by far, a DVR (digital video recorder).
Enter the brand new computer. It turns out that a computer with a TV tuner card can make a dandy DVR, and this new one with lots of power, high-quality graphics, and Windows Vista Ultimate with Media Center is a perfect candidate.
TV Tuner Card:
I have Windows Vista 64 with Media Center, so I ordered the AverMedia Media Center Upgrade Kit from NewEgg.com, a PCI-E tuner card. I chose that product for its features but even more because of the good recommendations from purchasers on NewEgg.com. The card includes two tuners, one for analog channels (broadcast or cable) and the other for digital (broadcast or cable).
Installation:
I installed it in a PCI-E slot, rebooted, and Windows automatically installed the drivers. There was no need to use the drivers on the included CD-ROM; I'm confident that Windows used appropriate drivers. With the kit also came a remote control and remote receiver, for which Windows also found and installed a driver.

I connected the cable TV signal to the analog tuner, and the included "test" antenna to the digital tuner, and immediately tuned in all of the analog cable channels and eight digital broadcast channels.
I'm not an HDTV enthusiast, at least not yet. I know almost nothing about home-theater PC (HTPC). But this was trivially simple. What we have here is a card that is designed to work specifically with Windows Media Center (MC), a Microsoft software package found on some XP and Vista machines. The card came with no other software except drivers - it would be useless without MC, and MC cannot play or record TV signals without a TV tuner card. They go together hand in glove, and they worked together right out of the box with no coaxing at all.
Performance:
- The quality of the analog cable programs is better than my desktop TV, and they have equal signals off the same splitter.
- The quality of the digital programs is stunning.
- MC and the tuner immediately detected and cataloged every useful analog cable channel.
- Using a tiny "test" antenna supplied with the kit, the system detected all of the major local broadcast stations. That test antenna is all I need.
- MC can play one program from one tuner while recording another program from the other tuner.
- With MC not running, the computer's CPU usage is 1% to 2%. With MC playing a program it is about 20%, and with MC both playing and recording it is about 25%.
- The card's tuner chips felt warm to the touch, but not hot.
- I ran a CPU exercise program called HeavyLoad while MC was playing and recording, and the program played without a hitch with CPU usage bumping up between 90% and 100%. Nothing overheated.
- The documentation was nonexistent. I have no idea how some of the included parts are even supposed to be used.
- It has no FM tuner, which would be very nice with MC.
- Though there are two tuners on the card, MC will not show picture-in-picture.
- The tuner is capable of playing QAM (unencrypted digital cable signals) but MC will not take advantage that capability.
It works exactly as advertised and I'm glad to have it. I wonder if we should just build another, cheaper computer and dedicate it to DVR as a replacement for the VCR. Still expensive I guess.
An alternative is to rent the DVR from our cable provider Comcast, which would require us to upgrade the cable from Standard to Digital, and the rental plus the upgrade would cost us $16.00/month or about $200.00/year. At that rate we coud pay for an $800 computer in four years ... hmmm.
Tuesday, December 11, 2007
TrueCrypt Is Cool
My business requires me to safeguard the security of certain files. For years I have used Encrypted Magic Folders (EMF) from PC-Magic to encrypt those files, and to hide them from the view of an interloper. I loved it, because files were always encrypted on disk and yet were fully accessible to applications. However, when I upgraded to Vista 64, the new EMF crashed my system so completely that it was unbootable even in safe mode. I tried it twice, recovered twice with some difficulty, and gave up on EMF.
In the meantime I had heard about TrueCrypt, an open-source disk encryption package for Windows and Linux. It's free! I must admit that after I downloaded it, I needed some time to get my mind around it.
Here are the basics:
That's the simple view of TrueCrypt. There is lots more. For example:
In the meantime I had heard about TrueCrypt, an open-source disk encryption package for Windows and Linux. It's free! I must admit that after I downloaded it, I needed some time to get my mind around it.
Here are the basics:
- Using the TrueCrypt application you create a large "container" file on your system, larger than you will need to hold your encrypted files. It can be on any read/write disk, even a memory stick, and is initially filled with random data.
- The container file can be copied, moved, deleted, or renamed just like any other file. It's not fragile. It can have any name and any file extension. You can have more than one.
- With the TrueCrypt application, you mount that container file as a disk volume with its own drive letter. You choose the letter.
- The TrueCrypt application runs in the background and manages TrueCrypt volumes.
- Within the TrueCrypt volume you create folders, or copy them in, and create or copy in any files that ought to be encrypted. A TrueCrypt volume behaves exactly like any other disk, even though it's really just a file on your hard drive or mem stick. Every file within it is totally encrypted, including file names and even its file system.
- Unused space in the TrueCrypt container file is filled with random data which cannot be distinguished from actual encrypted files.
- When you open an encrypted file in an application, such as a wordprocessor or graphic editor, the file is decrypted on the fly so that the application sees it decrypted.
- The file is never decrypted on disk, however, unless the application keeps temporary backup copies, and of course you should tell your applications to keep those in an encrypted volume too.
- Backup of encrypted data is easy: Just dismount the encrypted volume and copy its container file, still encrypted, to the backup medium.
- If the backup medium is another disk, mem stick, DVD, or CD-ROM, you can actually mount that backup container file whenever you want without ever copying it back to the original hard disk.

That's the simple view of TrueCrypt. There is lots more. For example:
- Anyone examining your system or your disk can tell that you use TrueCrypt, and can probably even identify the container files.
- However, you can host a TrueCrypt volume within another truecrypt volume in a manner that makes the internal volume both hidden and undectable even if the outer volume is mounted and visible. Really cool. The TrueCrypt people call this "plausible deniability," and consider it quite important.
- Example: An adversary points a gun at you and demands to see your encrypted files. You can give them the password to the outer encrypted volume without ever revealing that an inner, hidden volume even exists. It's invisible. I don't actually see the need for a hidden volume in my business, but evidently some folks do.
- You can host a truecrypt volume on a public computer, or another person's computer, without installing any software on that computer, so your encrypted files are portable.
- You can tell TrueCrypt to mount certain TrueCrypt volumes automatically at bootup, though you will be required to enter a password to complete the mounting process.
- TrueCrypt allows you to use any of eight different encryption algorithms and three different hash algorithms, making decryption by an adversary even more difficult.
Labels:
64-bit,
Backup,
computer,
data encryption,
hard drive,
TrueCrypt,
Vista
Sunday, December 2, 2007
RAID Backup
Working perfectly!
Usually, a person needs a backup when their disk drive fails. All disk drives fail sometime - there is no escape from that truth. But there are other reasons for keeping good backups:
Drive Failure:
Disk drive failure can mostly be avoided by using two mirrored drives in a configuration known as RAID 1. RAID means Redundant Array of Independent Drives, and has several well-defined levels. RAID 1 is a simple comfiguration with two drives which always contain exactly the same information, hence the term "mirrored." If either drive fails, the other simply becomes the system's sole drive and takes over without a hitch. Since the probability of two drives failing at once is very small, RAID 1 pretty well covers that problem. The new computer here employs RAID 1.
Total Disaster:
If the building burns down or floods, the only solution is to have a separate backup stored offsite. This can be on the internet, another building some distance away, or perhaps in a fire- and water-proof safe. At this office a flood is highly unlikely, so we store encrypted DVD backups of most user files in a fire-resistant safe in the basement, and we occasionally put a DVD in a safe deposit box at the bank. I have just set up an upload account and I may stop putting DVDs in the safe deposit box. We'll see.
Deliberate Mischief, or Accidental Deletion or Modification:
RAID disks don't help here, because the RAID disk controller keeps the two mirrored disks identical even when the files themselves are deleted or corrupted. This is where Windows System Restore can be very handy indeed. I have several times seen a serious problem solved by restoring a system to a previous date and time. System Restore works, though it has the disadvantage that the whole drive reverts to a selected time in the past, even if you only need to recover one file.
 But if System Restore isn't the solution, then backups are the answer. DVD and internet backups can be used to restore user data, but what about all of the rest of the system? I started a full backup once, but quit when the backup wizard pointed out that I would need 19 DVDs. Enter "RAID Backup" with a third identical disk drive. At some reasonable interval (every day, every week, every month) I can disconnect the power to one of the two mirrored disks and connect the third disk. The disconnected disk is instantly a complete backup of everything, and the newly-connected disk will soon be overwritten and re-mirrored to the remaining good disk in the RAID 1 pair. Voila - complete backup in about five minutes for a one-time cost of about $80. It does actually take about 2 hours and 15 minutes to re-mirror, but the system is usable, if slower, while that takes place. And the third disk, with no power, is safe from any mischief.
But if System Restore isn't the solution, then backups are the answer. DVD and internet backups can be used to restore user data, but what about all of the rest of the system? I started a full backup once, but quit when the backup wizard pointed out that I would need 19 DVDs. Enter "RAID Backup" with a third identical disk drive. At some reasonable interval (every day, every week, every month) I can disconnect the power to one of the two mirrored disks and connect the third disk. The disconnected disk is instantly a complete backup of everything, and the newly-connected disk will soon be overwritten and re-mirrored to the remaining good disk in the RAID 1 pair. Voila - complete backup in about five minutes for a one-time cost of about $80. It does actually take about 2 hours and 15 minutes to re-mirror, but the system is usable, if slower, while that takes place. And the third disk, with no power, is safe from any mischief.
 It Works!:
It Works!:
I wasn't entirely sure that the Intel software would be totally cool with what I wanted to do, but I tried it last night and today. The system has three identical 320 Mb Western Digital hard disk. Steps in the experiment:
 Windows Experience Index:
Windows Experience Index:
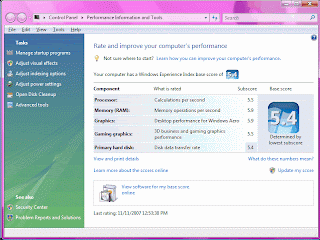
Before these little experiments, the system's Windows Experience Index was 5.4, limited by the disk subscore of 5.4. I ran the tests several times. Since the experiments, the Windows Experience Index is 5.5, limited by both the processor and gaming graphics, with the disk subscore improving to 5.7. Why did the disk subscore go up from 5.4 to 5.7, using exactly the same disks? Only Microsoft knows.
Usually, a person needs a backup when their disk drive fails. All disk drives fail sometime - there is no escape from that truth. But there are other reasons for keeping good backups:
- Total disaster, such as a fire or flood that destroys the whole computer and all nearby backups.
- Deliberate mischief, such as a virus that deletes important files.
- Accidental deletion or modification of one or more files.
Drive Failure:
Disk drive failure can mostly be avoided by using two mirrored drives in a configuration known as RAID 1. RAID means Redundant Array of Independent Drives, and has several well-defined levels. RAID 1 is a simple comfiguration with two drives which always contain exactly the same information, hence the term "mirrored." If either drive fails, the other simply becomes the system's sole drive and takes over without a hitch. Since the probability of two drives failing at once is very small, RAID 1 pretty well covers that problem. The new computer here employs RAID 1.
Total Disaster:
If the building burns down or floods, the only solution is to have a separate backup stored offsite. This can be on the internet, another building some distance away, or perhaps in a fire- and water-proof safe. At this office a flood is highly unlikely, so we store encrypted DVD backups of most user files in a fire-resistant safe in the basement, and we occasionally put a DVD in a safe deposit box at the bank. I have just set up an upload account and I may stop putting DVDs in the safe deposit box. We'll see.
Deliberate Mischief, or Accidental Deletion or Modification:
RAID disks don't help here, because the RAID disk controller keeps the two mirrored disks identical even when the files themselves are deleted or corrupted. This is where Windows System Restore can be very handy indeed. I have several times seen a serious problem solved by restoring a system to a previous date and time. System Restore works, though it has the disadvantage that the whole drive reverts to a selected time in the past, even if you only need to recover one file.
 But if System Restore isn't the solution, then backups are the answer. DVD and internet backups can be used to restore user data, but what about all of the rest of the system? I started a full backup once, but quit when the backup wizard pointed out that I would need 19 DVDs. Enter "RAID Backup" with a third identical disk drive. At some reasonable interval (every day, every week, every month) I can disconnect the power to one of the two mirrored disks and connect the third disk. The disconnected disk is instantly a complete backup of everything, and the newly-connected disk will soon be overwritten and re-mirrored to the remaining good disk in the RAID 1 pair. Voila - complete backup in about five minutes for a one-time cost of about $80. It does actually take about 2 hours and 15 minutes to re-mirror, but the system is usable, if slower, while that takes place. And the third disk, with no power, is safe from any mischief.
But if System Restore isn't the solution, then backups are the answer. DVD and internet backups can be used to restore user data, but what about all of the rest of the system? I started a full backup once, but quit when the backup wizard pointed out that I would need 19 DVDs. Enter "RAID Backup" with a third identical disk drive. At some reasonable interval (every day, every week, every month) I can disconnect the power to one of the two mirrored disks and connect the third disk. The disconnected disk is instantly a complete backup of everything, and the newly-connected disk will soon be overwritten and re-mirrored to the remaining good disk in the RAID 1 pair. Voila - complete backup in about five minutes for a one-time cost of about $80. It does actually take about 2 hours and 15 minutes to re-mirror, but the system is usable, if slower, while that takes place. And the third disk, with no power, is safe from any mischief. It Works!:
It Works!:I wasn't entirely sure that the Intel software would be totally cool with what I wanted to do, but I tried it last night and today. The system has three identical 320 Mb Western Digital hard disk. Steps in the experiment:
- Disk Drives A and B were mirrored, drive C was powered up as a spare but had never been used.
- I shut down the computer, disconnected power on B, rebooted the computer. The Bios complained that the RAID 1 pair was "degraded" and gave me a chance to deal with it in the Bios, but I declined and let the bootup proceed.
- The computer booted normally, and the Intel monitor software presented a pop-up balloon that said the RAID 1 disk was degraded but could be repaired.
- I clicked on the balloon and followed the instructions to restore disk C to mirror the good disk in the RAID pair, disk A. Two and a quarter hours later, A & C were a mirrored RAID pair and B was a complete backup. Job done.
- As an experiment, however, I shut down again and disconnected all EXCEPT disk B, then rebooted. Again the Bios complained and the on-line software did too, but the system functioned normally on just the "backup" disk. As far as I could tell, all files were accessible. The RAID software, apparently confused, also created a second RAID array at this point, consisting of Disk B and a "missing" disk. Duh.
- I rebooted with only A & C connected, and everything worked once again, no complaints.
- Then I connected B as well, rebooted, and got some complaints about a degraded pair in the second RAID array (disk B), but the system ran normally and all files on all disks seemed to be accessible, including the files on disk B.
- Finally, I disconnected disk C, leaving A & B connected, and rebooted once again. The Bios and the Intel application software both complained about degraded RAID arrays. But it allowed me to delete the second RAID array, consisting of only disk B. That done, it allowed me to re-mirror B to the good disk in the original RAID pair, disk A, even though disk B contained lots of valid data. I was concerned that it might not let me destroy data, and I think there were at least four warnings that data would be destroyed on disk B if I proceeded, but it finally let me do it. Now disk C is again the full backup and the system is back to a RAID array of disks A & B.
 Windows Experience Index:
Windows Experience Index:Before these little experiments, the system's Windows Experience Index was 5.4, limited by the disk subscore of 5.4. I ran the tests several times. Since the experiments, the Windows Experience Index is 5.5, limited by both the processor and gaming graphics, with the disk subscore improving to 5.7. Why did the disk subscore go up from 5.4 to 5.7, using exactly the same disks? Only Microsoft knows.
Sunday, November 11, 2007
Heat, Speed, & Sound
Speed:
Mr. Tobias Schonherr pointed out an error in my assembly of this new computer. Thank you Mr. Schonherr! I had misinterpreted the Intel manual on the DP35DP motherboard, and unwittingly installed the two memory modules in single-channel mode rather than dual-channel mode.
As I understand it, dual-channel mode enables the CPUs to make two requests on memory at one time, increasing overall memory throughput. See below. First the memory modules before and after, then the resulting Windows Experience Index before and after. The computer recognized 4 Gb of memory in each case, but you will notice that the memory sub-index jumped from 5.6 to 5.9, now as high as any other element of the system and higher than the dual-processor CPU.
Heat:
Modern computers contain a host of self-monitoring devices, temperature monitors in particular. I installed the Intel Desktop Utilities, which takes advantage of those devices to provide readouts and to raise an alarm if some device goes outside its limit.
A few days back I returned to my computer to find an alarm on the screen. The CPU had exceeded its temperature limit of 68 degrees C for several minutes, going as high as 69 C (156 F). I downloaded a system-exerciser program called HeavyLoad and ran the CPU test, which is a repetitive graphics application, and the CPU temperature jumped right up to 70 C, CPU fan becoming very audible. Oops - problem.
I wondered if the thermal transfer between the CPU and its heatsink was OK. I had removed the heatsink once to re-check that the CPU was correctly loaded in its socket, thus disturbing the termal transfer compound. Also I had never felt good about the seating of the clips that hold the heatsink to the motherboard.
So I removed the heatsink once again, removed the old thermal transfer compound, and applied Arctic Silver compound in its place, evening it out with a credit card. Replacing the heatsink atop the CPU cover, I tried very carefully this time to apply equal pressure on all of the mounting clips, hearing a satisfying little click at each corner, an assurance that the heatsink is held down squarely. I also disconnected the internal case fan from motherboard control and connected it to full voltage so that it will always run full speed. It's noiseless anyway.
Good results! The following measurements were made with HeavyLoad executing its graphic application (about 60% CPU utilization), and the hole pattern in the back of the case blocked, thus forcing air to come all the way through from the front). In each case, temperatures were allowed to settle for at least a quarter of an hour. The CPU fan is automatically controlled from the motherboard:
I wish it were cooler still, but the CPU is now well within specifications. Further, the speed of the rear exhaust fan doesn't seem to make much difference in the temperatures, though it makes a lot of difference in noise. So I'm leaving the fan on low until there is a problem.
Noise:
I admit that my hearing isn't what it once was, but this system is so quiet that I can't always be sure I'm hearing it. A very low rumble from the disk drives is about all there is, and only when they are busy. But when the forced-air-furnace comes on I just can't hear it at all. I LOVE that! Now about that furnace ...
Mr. Tobias Schonherr pointed out an error in my assembly of this new computer. Thank you Mr. Schonherr! I had misinterpreted the Intel manual on the DP35DP motherboard, and unwittingly installed the two memory modules in single-channel mode rather than dual-channel mode.
As I understand it, dual-channel mode enables the CPUs to make two requests on memory at one time, increasing overall memory throughput. See below. First the memory modules before and after, then the resulting Windows Experience Index before and after. The computer recognized 4 Gb of memory in each case, but you will notice that the memory sub-index jumped from 5.6 to 5.9, now as high as any other element of the system and higher than the dual-processor CPU.
| Before | After | |
 |
 | |
 |
 |
Heat:
Modern computers contain a host of self-monitoring devices, temperature monitors in particular. I installed the Intel Desktop Utilities, which takes advantage of those devices to provide readouts and to raise an alarm if some device goes outside its limit.
A few days back I returned to my computer to find an alarm on the screen. The CPU had exceeded its temperature limit of 68 degrees C for several minutes, going as high as 69 C (156 F). I downloaded a system-exerciser program called HeavyLoad and ran the CPU test, which is a repetitive graphics application, and the CPU temperature jumped right up to 70 C, CPU fan becoming very audible. Oops - problem.
I wondered if the thermal transfer between the CPU and its heatsink was OK. I had removed the heatsink once to re-check that the CPU was correctly loaded in its socket, thus disturbing the termal transfer compound. Also I had never felt good about the seating of the clips that hold the heatsink to the motherboard.
So I removed the heatsink once again, removed the old thermal transfer compound, and applied Arctic Silver compound in its place, evening it out with a credit card. Replacing the heatsink atop the CPU cover, I tried very carefully this time to apply equal pressure on all of the mounting clips, hearing a satisfying little click at each corner, an assurance that the heatsink is held down squarely. I also disconnected the internal case fan from motherboard control and connected it to full voltage so that it will always run full speed. It's noiseless anyway.
Good results! The following measurements were made with HeavyLoad executing its graphic application (about 60% CPU utilization), and the hole pattern in the back of the case blocked, thus forcing air to come all the way through from the front). In each case, temperatures were allowed to settle for at least a quarter of an hour. The CPU fan is automatically controlled from the motherboard:
| Conditions | CPU | MOB | ICH | MCH | GPU | CPU |
| C | C | C | C | C | Fan | |
| Max allowed | 68 | 85 | 119 | 109 | RPM | |
| Exhaust fan LOW (silent) | 60 | 48 | 62 | 66 | 53 | 1467 |
| Exhaust fan MED (audible) | 60 | 49 | 62 | 66 | 50 | 1345 |
| Exhaust fan HI (whoosh) | 59 | 47 | 62 | 66 | 50 | 1348 |
| Fan LOW, no HeavyLoad | 40 | 41 | 63 | 66 | 53 | 927 |
I wish it were cooler still, but the CPU is now well within specifications. Further, the speed of the rear exhaust fan doesn't seem to make much difference in the temperatures, though it makes a lot of difference in noise. So I'm leaving the fan on low until there is a problem.
Noise:
I admit that my hearing isn't what it once was, but this system is so quiet that I can't always be sure I'm hearing it. A very low rumble from the disk drives is about all there is, and only when they are busy. But when the forced-air-furnace comes on I just can't hear it at all. I LOVE that! Now about that furnace ...
Subscribe to:
Comments (Atom)
