Windows 11 sort of sneaked up on me. My fault of course, not paying attention, but Microsoft says October 5, 2021, less than three weeks from today. We'll see.
Of course even the old laptop might be upgraded to meet the Windows 11 requirements, and perhaps some of the requirements might not really be necessary to get Windows 11 running. For example, that ancient laptop has neither a discrete TPM nor a firmware TPM, but it has BitLocker encryption working just fine and quite securely on its (one and only) disk drive anyway. Experience will tell us what will actually work with Windows 11.
Microsoft did have an application called the "PC Health Check App," which could run on a destination computer and determine whether that computer met their Windows 11 requirements, but the scuttlebutt is that it was thoroughly flawed (with source code unavailable of course) and it has been withdrawn. As of today, September 17, the page for it still says "COMING SOON." It's been coming soon for a while now.
However, there is a page on Microsoft.com which does purport to set forth the requirements for Windows 11. Happily, there are others besides Microsoft who have read these requirements and put them in an application. In particular, there is a Windows application called WhyNotWin11.exe on GitHub: This app is open source and peer reviewed (unlike any Microsoft apps), written by by Robert Maehl, downloaded 869,000 times so far. Might be a good thing to support.
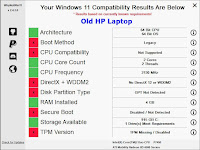
WhyNotWin11.exe puts all of Microsoft's Windows 11 stated requirements into a nice display. You see two of those displays here. One is for a twelve-year-old HP Dv7t laptop, which has been updated from Windows Vista all the way to Windows 10. That one shows a lot of Windows 11 deficiencies. The other is for the Forte computer, built just this summer, showing no deficiencies.
 |
| Bill of Materials |
Forte did initially have a deficiency, according to WhyNotWin11: The Vision Tech Radeon 5450 Graphics Card did not meet the Win 11 DirectX or WDDM requirements. Therefore that card has been replaced by the ASUS NVIDIA GT710 “4H SL 2GD5" Graphics Card, which I know will qualify and which is probably better anyway. See the revised Bill of Materials.
By the way, Forte is for sale. You can see what it cost, and I do expect to receive some benefit from my work in building it, so make me an offer. Note, however, that I will not ship it, and will only deliver it in the Twin Cities Minnesota metropolitan area. It can come with Windows 10 or Windows 11, your choice. Either way, it's a really hot computer!